
This is a thorough campaign the American Bankers Association (ABA) put together to keep you aware of red flags of phishing. It includes tips for email, phone, text and mobile payment app scams.

Banks Never Ask That Website
Head over to Banks Never Ask That and see how you can protect yourself from the never ending fraudulent activity that we as consumers see every day.
Vishing is just one form of phishing, which is any type of message — such as an email, text, phone call or direct-chat message — that appears to be from a trusted source, but isn’t. The goal is to steal someone's identity or money.

What is vishing? Tips for spotting and avoiding voice scams
When your phone rings, it’s sometimes hard to know who’ll be on the other end. It might be someone vishing.
Vishing, a combination of ‘voice’ and ‘phishing,’ is a phone scam designed to get you to share personal information. In 2018, phishing crimes cost victims $48 million, according to the FBI’s Internet Crime Complaint Center.
Here’s what to know about vishing attacks and how to help protect yourself.
What is vishing?
During a vishing phone call, a scammer uses social engineering to get you to share personal information and financial details, such as account numbers and passwords. The scammer might say your account has been compromised, claim to represent your bank or law enforcement, or offer to help you install software. Warning: It’s probably malware.
Vishing is just one form of phishing, which is any type of message — such as an email, text, phone call or direct-chat message — that appears to be from a trusted source, but isn’t. The goal is to steal someone’s identity or money.
It’s getting easier to contact more people, too. Scammers can place hundreds of calls at a time using voice over internet protocol (VoIP) technology and can spoof the caller ID to make the call appear to come from a trusted source, such as your bank.
Common vishing scams
About three-quarters of the fraud complaints reported to the Federal Trade Commission involve contact with consumers by telephone. Here are some of the common themes:
“Compromised” bank or credit card account
Whether it’s a person or a prerecorded message on the other end, you’ll be told there’s an issue with your account or a payment you made. You may be asked for your login credentials to fix the problem or asked to make a new payment. Instead of giving out your info, hang up and call your financial institution on their publicly available number.
Unsolicited loan or investment offers
Scammers will call with offers that are too good to be true. They’ll say, for example, that you can earn millions of dollars on one small investment, pay off all your debt with one quick fix, or get all your student loans forgiven in one fell swoop. Typically, you must “act now” and will need to pay a small fee. Don’t fall for it. Legitimate lenders and investors won’t make these types of offers and won’t initiate contact out of the blue.
Medicare or Social Security scam
Phone calls are the No. 1 method scammers use to reach older adults, according to the Federal Trade Commission. Crooks pose as Medicare reps — often during Medicare open enrollment season — and try to glean financial information from the victim, such as their Medicare number or bank account details. Then the scammer will either fraudulently use the victim’s Medicare benefits or steal their money. Scammers may also claim to be from the Social Security Administration and threaten to suspend or cancel the victim’s Social Security number.
IRS tax scam
There are many variations of this type of scam, but typically, you’ll receive a prerecorded message. It tells you something’s wrong with your tax return and if you don’t call back, a warrant will be issued for your arrest. Scammers usually pair this with a spoofed caller ID made to look like the call is coming from the IRS. Before you proceed, it pays to understand what the IRS can and can’t do when they need to contact you.
How to spot a vishing scam
Here are some of the tell-tale signs of a vishing scam:
- The caller claims to represent the IRS, Medicare, or the Social Security Administration. Unless you’ve requested contact, none of these federal agencies will ever initiate contact with you by email, text messages, or social media channels to request personal or financial information. In fact, be skeptical of anyone who calls you with an offer.
- There’s a frantic sense of urgency. Scammers will try to tap into your sense of fear, using threats of arrest warrants and problems with your account. If you get one of these phone calls, remain calm and never give out your own information. Hang up and do your own investigation.
- The caller asks for your information. They may ask you to confirm your name, address, birth date, Social Security number, bank account info, and other identifying details. To trick you into thinking they’re legit, they may even have some of this info on hand. The goal is to get the remaining info that they don’t have yet.
How to protect yourself from vishing
Aside from knowing how vishing works and looking for red flags, you can also:
- Join the National Do Not Call Registry. Adding your home or mobile phone number to this registry is free and tells telemarketers you don’t want their phone calls. However, certain types of organizations may still call you, such as charities and political groups, and it won’t stop people from illegally calling your number.
- Don’t pick up the phone. Although it may be tempting to answer every phone call, simply let them go to voicemail. Caller IDs can be faked, which means you might not know who’s calling. Listen to your messages and decide whether to call the person back.
- Hang up. The moment you suspect it’s a vishing phone call, don’t feel obliged to carry on a polite conversation. Simply hang up, and block the number.
- Don’t press buttons or respond to prompts. If you get an automated message that asks you to press buttons or respond to questions, don’t do it. For instance, the message might say “Press 2 to be removed from our list” or “Say ‘yes’ to talk with an operator.” Scammers often use these tricks to identify potential targets for more robocalls. They also might record your voice and later use it when navigating voice-automated phone menus tied to your accounts.
- Verify the caller’s identity. If the person provides a call-back number, it may be part of the scam — so don’t use it. Instead, search for the company’s official public phone number and call the organization in question.
How to recover after a vishing attack
If you’ve provided your financial information to someone who you later think is a scammer, first call your financial institution. Whether it’s your credit card issuer, bank, or Medicare contact, call and ask about canceling fraudulent transactions and blocking future charges.
You might also need to change your account numbers to make sure no one uses your existing accounts.
Freezing your credit reports can help ensure no one can open new accounts in your name. Then file a complaint with the Federal Trade Commission or the FBI’s Internet Crime Complaint Center.
While vishing attacks are crafted to trick you, it’s possible to learn the red flags before you pick up the phone. Stay ahead of the cyberthieves who are trying to tap your personal details over the phone.
Good cyber hygiene is a general practice that can help keep you safe and secure online, but there are several best practices to ensure your cyber hygiene is the best it can be. Read below to see what you can do to stay safe.

Good cyber hygiene habits to help stay safe online
Have you heard of something called cyber hygiene? Surely, brushing your teeth and taking showers isn’t something traditionally associated with technology — yet the term is a useful metaphor for needing to make smart decisions about your smart devices.
Good hygiene is something you’re taught as a child and something that generally sticks with you for the rest of your life. It involves three basic principles: using products and tools that fit your hygiene needs, performing these hygienic tasks correctly, and establishing a routine.
But what is cyber hygiene and what does it have to do with your computer and connected devices?
Cyber hygiene is about training yourself to think proactively about your cyber security — as you do with your daily personal hygiene — to resist cyber threats and online security issues. Unfortunately, cyber security still isn’t taken as seriously as cavities and root canals. Some people take cyber security for granted, but this may change, as cyber threats continue to evolve. In the meantime, establishing solid cyber hygiene practices should be as routine as brushing your teeth.
Here are a few tips to get you and your family thinking about good cyber hygiene practices.
Use the right tools for cyber hygiene
Ever try brushing your teeth without a toothbrush? Without the right tools for the job, maintaining personal hygiene would be a bit more difficult, if not impossible. The same is true for managing good cyber hygiene. Without the right products and tools, personal information you think is secure could, in fact, be at risk.
Reputable antivirus and malware software, a network firewall, and password protection all help to protect personal data stored on your home computer. Taken together, these tools may help you feel confident about the security of your home computer, laptop, smartphone, and other devices.
Additionally, you should always make sure the security brand is a reputable source before installing anything on your computer or other devices.
Be thorough, be accurate with cyber hygiene
Everyone is supposed to floss, right? But does everyone do it as much as the dentist recommends? Deleted or presumably irretrievable files on your computer require a kind of flossing and demand special attention from time to time.
For example, you may think that regularly emptying the trash can or recycle bin removes personal or sensitive data from the hard drive. This is not the case.
To permanently delete files from your computer, you must use data-wiping software. Whenever you introduce new software, add on hardware, or modify system files, you’re at risk of losing personal data. Get in the habit of regularly clearing out data you don’t need and making sure to wipe it clean from the hard drive.
Another area of security that requires your attention is password protection. Don’t get lazy and skimp on creating complex, unique passwords for each account, using combinations of at least 12 letters, numbers, and special characters. Change your account passwords regularly, and you’ll be on your way to better cyber hygiene in no time.
Make cyber hygiene part of your routine
Learning to monitor your cyber security regularly can increase your chances of avoiding an online threat. But just like any habit you wish to make stick, it requires routine and repetition.
Get started by setting an alarm or marking a calendar with dates to address a series of tasks — things such as scanning for viruses with antivirus software, updating the operating systems of all your devices, checking for security patches, wiping the hard drive, and changing your passwords. Once you begin to get the hang of cyber hygiene, it will become second nature to you.
Key steps for good cyber hygiene
Good cyber hygiene is a general practice that can help keep you safe and secure online, but there are several best practices to ensure your cyber hygiene is the best it can be. Here are nine essential steps.
Step 1: Install reputable antivirus and malware software
The first and maybe most important step is installing antivirus software. What is it designed to do? Antivirus software is a program or umbrella of programs that scans for and eradicates computer viruses and other malicious software, or malware. It’s a vital component of your overall cyber hygiene in its protection against security breaches, along with other threats.
Specifically, antivirus software provides protection by performing key tasks, including these.
- Pinpointing specific files for the detection of malicious software.
- Scheduling and performing automatic scans.
- Scanning either one particular file or your entire computer, or a flash drive, depending on your specific needs.
- Erasing malicious codes and software.
- Confirming the “health” of your computer and other devices.
Step 2: Use network firewalls
Using a network firewall is another key habit for maintaining good cyber hygiene. Firewalls are a first line of defense in network security by preventing unauthorized users from accessing your websites, mail servers, and other sources of information that can be accessed from the web.
Step 3: Update software regularly
Update your apps, web browsers, and operating systems regularly to ensure you’re working with the latest programs that have eliminated or patched possible glitches. Setting up this feature to update automatically will help ensure you have the latest protections.
These updates are particularly important because they often include software patches. Software developers issue security patches whenever they discover software flaws — flaws that could let in viruses or hackers. Developers may not always alert you when a critical patch has been implemented, because this might give hackers the heads-up, as well. Thus, regular updates will ensure these patches plug any holes in your software.
Step 4: Set strong passwords
Setting strong passwords for all of your devices is essential. Your passwords should be unique and complex, containing at least 12 characters along with numbers, symbols, and capital and lowercase letters. Changing your passwords regularly — and never sharing or reusing the same password — will help prevent hackers from figuring them out.
Additional device controls are firmware passwords. These are hardware passwords that help prevent others from using your computer. While disk encryption prevents cyberthieves from accessing information stored on your device, firmware passwords protect your hardware by preventing your machine from being rebooted or reset without your password.
Step 5: Use multi-factor authentication
Two-factor or multi-factor authentication is a best practice that offers an additional layer of protection. Two-factor authentication usually requires you to submit your password and username along with, say, a unique code that is sent to your cell phone. This may be all that is needed for some systems, but multi-factor authentication adds additional layers of security with the use of biometrics, like facial or fingerprint recognition, to make it harder for hackers to gain access to your device and personal information.
Step 6: Employ device encryption
While most companies automatically have data encryption processes in place, you also may want to encrypt your devices and other media that contain sensitive data — including laptops, tablets, smartphones, removable drives, backup tapes, and cloud storage. In fact, many devices use encryption as the default for data stored on smartphones. Some apps are using end-to-end encryption, and other services encrypt data on your devices and back them up in the cloud. Another option is to use an encrypted USB memory stick for protecting sensitive data.
Step 7: Back up regularly
It’s also smart to keep your files secure by backing up important files offline, on an external hard drive, or in the cloud. This can help protect against many types of data loss, especially if hackers gain access to one of your devices.
Step 8: Keep your hard drive clean
If you’re selling your laptop, tablet or smartphone, it’s important to ensure your personal or sensitive information doesn’t get passed along, as well. If your device is hacked, a clean hard drive means less information that’s accessed.
But merely deleting files or data may not be enough. Part of good cyber hygiene is reformatting and then wiping your hard drive clean. For example, if you want to sell your computer and have used it for online banking, you’ll want to consider disk-wiping to remove software and data from your hard drive.
Step 9: Secure your router
Don’t forget to protect your wireless network. This involves turning off and updating the default name and password the router came with from the manufacturer, turning off remote management, and logging out as the administrator once it’s set up. Also, make sure your router offers WPA2 or WPA3 encryption to maintain the highest level of privacy of information sent via your network.
Remember, it’s smart to practice good cyber hygiene habits. If you set up your computer and other devices with reputable antivirus programs, update them regularly, create strong passwords, and keep everything clean, you’ll be on your way to creating cyber habits that may help keep you safe and secure online.
A password is the key to your identity online - you wouldn't use a rubber band to lock your home, so don't fall for the repetitive use of simple passwords that protect your online presence.

How to choose a secure password
Strong passwords are the key to your digital life. Be sure to protect your information by utilizing the tips provided in this article.
Strong passwords are the key to your digital life. Be sure to protect your information by utilizing the tips provided in this article.
Digital keys
Passwords are the digital keys to our networks of friends, our work colleagues, and even our banking and payment services. We want to keep our passwords private to protect our personal lives, and that includes our financial information. While some cybercriminals may want to hack into our social networking or email accounts, most want the financial gain that hacking bank accounts can bring.
The most important two passwords are those for your email and social network accounts. If someone gains access to your email account, they could use the “forgot your password?” link on other websites you use, like online shopping or banking sites. If a hacker gets into your social network, they have the ability to scam your friends by sending out links to dangerous websites or posting fraudulent messages asking for money. The bottom line is that a good password is all that may stand between you and a cybercriminal.
How is it done?
There are many ways that hackers can crack your password outside of phishing attempts and spyware. One method is by attempting to log on to your account and guessing your password based off of personal information gained from your security questions. This is why it is extremely important not to include any personal information in your passwords.
Another way that hackers can attempt to gain access to your password is via a password cracker. A password cracker uses brute force by using multiple combinations of characters repeatedly until it gains access to the account.
The shorter and less complex your password is, the quicker it can be for the program to come up with the correct combination of characters. The longer and more complex your password is, the less likely the attacker will use the brute force method, because of the lengthy amount of time it will take for the
program to figure it out. Instead, they’ll use a method called a dictionary attack, where the program will cycle through a predefined list of common words that are used in passwords.
How You Can Create a Secure Password
In order to avoid being a victim of these kinds of hacks, we’ve amassed a collection of Do’s and Don’ts on how to choose a secure user password*.
*A secure password is one a hacker can’t easily guess or crack using software tools and one that is unique and complex.
Do use Two-Factor Authentication (2FA) whenever possible. 2FA adds another layer of security to any account you may be logging into. When using 2FA, you can choose two of three types of identification to provide:
- A password or pin number.
- A tangible item such as the last 4 digits of a credit card in your possession or a mobile device that a code can be sent to.
- A part of you such as a fingerprint or voiceprint.
Do use a combination of uppercase and lowercase letters, symbols and numbers.
Don’t use commonly used passwords such as 123456, the word “password,” “qwerty”, “111111”, or a word like, “monkey”.
Do make sure your user passwords are at least eight characters long. The more characters and symbols your passwords contain, the more difficult they are to guess.
Don’t use a solitary word in any language. Hackers have dictionary-based systems to crack these types of passwords. If you insist on using a word, misspell it as much as possible, or insert numbers for letters. For example, if you want to use the phrase “I love chocolate” you can change it to @1L0v3CH0c0L4t3!
Don’t use a derivative of your name, the name of a family member or the name of a pet. In addition to names, do not use phone numbers, addresses, birthdays or Social Security numbers.
Don’t use the same password across multiple websites. If remembering multiple passwords is an issue, you can use a password manager such as Norton Identity Safe to securely store your passwords.
Do use abbreviated phrases for passwords. You can choose a phrase such as “I want to go to England.” You can convert this phrase to an abbreviation by using the first letters of each word and changing the word “to” to a number “2.” This will result in the following basic password phrase: iw2g2e. Make it even more complex by adding punctuation, spaces or symbols: %iw2g2e!@
Don’t write your passwords down, share them with anyone or let anyone see you log into devices or websites.
Do change your passwords regularly.
Do log out of websites and devices when you are finished using them.
Don’t answer “yes” when prompted to save your password to a particular computer’s browser. Instead, rely on a strong password committed to memory or stored in a dependable password management program. Norton Security stores your passwords securely and fills them in online in encrypted form.
This may seem like a long, complicated process to go through just to log into a website, however, it is not as complicated as a cybercriminal gaining access to your passwords and stealing your identity. Just remember that a bit of legwork now can protect you from extremely compromising situations in the long run.
Know how to prevent an online scam from ever happening - read below for tips and tricks to stay vigilant against cybercrime in a cyber world.

11 ways to help protect yourself against cybercrime
Written by Alison Grace Johansen for NortonLifeLock
Cybercrime is an ongoing threat.
You might think that the only form of cybercrime you have to worry about is hackers stealing your financial information. But it may not be so simple. There are far more concerns than just basic financial ones. Cybercrime continues to evolve, with new threats surfacing every year.
When you hear and read about the range of cybercrimes out there, you might be tempted to stop using the internet entirely. That’s probably too drastic.
Instead, it’s a good idea to know how to recognize cybercrime, which can be the first step to helping protect yourself and your data. Taking some basic precautions and knowing who to contact when you see others engaged in criminal activities online are also important steps.
You might want to learn how to prevent cybercrime, but here’s the thing: You can’t. You can, however, take precautions to help protect against it.
What is cybercrime?
Cybercrime is any crime that takes place online or primarily online. Cybercriminals often commit crimes by targeting computer networks or devices. Cybercrime can range from security breaches to identity theft.
Other cybercrimes include things like “revenge porn,” cyber-stalking, harassment, bullying, and child sexual exploitation.
Terrorists collaborate on the internet, moving terrorist activities and crimes into cyberspace.
How to protect yourself against cybercrime
Anyone using the internet should exercise some basic precautions. Here are 11 tips you can use to help protect yourself against the range of cybercrimes out there.
1. Use a full-service internet security suite
For instance, Norton Security provides real-time protection against existing and emerging malware including ransomware and viruses, and helps protect your private and financial information when you go online.
2. Use strong passwords
Don’t repeat your passwords on different sites, and change your passwords regularly. Make them complex. That means using a combination of at least 10 letters, numbers, and symbols. A password management application can help you to keep your passwords locked down.
3. Keep your software updated
This is especially important with your operating systems and internet security software. Cybercriminals frequently use known exploits, or flaws, in your software to gain access to your system. Patching those exploits and flaws can make it less likely that you’ll become a cybercrime target.
4. Manage your social media settings
Keep your personal and private information locked down. Social engineering cybercriminals can often get your personal information with just a few data points, so the less you share publicly, the better. For instance, if you post your pet’s name or reveal your mother’s maiden name, you might expose the answers to two common security questions.
5. Strengthen your home network
It’s a good idea to start with a strong encryption password as well as a virtual private network. A VPN will encrypt all traffic leaving your devices until it arrives at its destination. If cybercriminals do manage to hack your communication line, they won’t intercept anything but encrypted data. It’s a good idea to use a VPN whenever you a public Wi-Fi network, whether it’s in a library, café, hotel, or airport.
6. Talk to your children about the internet
You can teach your kids about acceptable use of the internet without shutting down communication channels. Make sure they know that they can come to you if they’re experiencing any kind of online harassment, stalking, or bullying.
7. Keep up to date on major security breaches
If you do business with a merchant or have an account on a website that’s been impacted by a security breach, find out what information the hackers accessed and change your password immediately.
8. Take measures to help protect yourself against identity theft
Identity theft occurs when someone wrongfully obtains your personal data in a way that involves fraud or deception, typically for economic gain. How? You might be tricked into giving personal information over the internet, for instance, or a thief might steal your mail to access account information. That’s why it’s important to guard your personal data. A VPN — short for virtual private network — can also help to protect the data you send and receive online, especially when accessing the internet on public Wi-Fi.
9. Know that identity theft can happen anywhere
It’s smart to know how to protect your identity even when traveling. There are a lot of things you can do to help keep criminals from getting your private information on the road. These include keeping your travel plans off social media and being using a VPN when accessing the internet over your hotel’s Wi-Fi network.
10. Keep an eye on the kids
Just like you’ll want to talk to your kids about the internet, you’ll also want to help protect them against identity theft. Identity thieves often target children because their Social Security number and credit histories frequently represent a clean slate. You can help guard against identity theft by being careful when sharing your child’s personal information. It’s also smart to know what to look for that might suggest your child’s identity has been compromised.
11. Know what to do if you become a victim
If you believe that you’ve become a victim of a cybercrime, you need to alert the local police and, in some cases, the FBI and the Federal Trade Commission. This is important even if the crime seems minor. Your report may assist authorities in their investigations or may help to thwart criminals from taking advantage of other people in the future. If you think cybercriminals have stolen your identity. These are among the steps you should consider.
- Contact the companies and banks where you know fraud occurred.
- Place fraud alerts and get your credit reports.
- Report identity theft to the FTC.
How you can help by following the 11 tips
In a way, fighting cybercrime is everybody’s business. Think of it as an obligation to do your part in the fight against cybercrime.
For most people, that means following a few simple, common-sense steps to keep yourself and your family safe. It also means reporting cybercrimes to relevant officials at the appropriate time.
When you do, you’re helping to fight cybercrime.
Is your inbox full of unsolicited emails that may or may not be spam? Cleaning up your online mailbox is easy - read below on what you can do to prevent those emails from ever getting to your inbox.

How to get rid of spam emails
Generally, legitimate marketing emails are sent by businesses once you opt in to receive them. They allow you to subscribe to a newsletter, sign up for services, read members-only content, or share messages via email and social media.
Spam messages often come from illegitimate email addresses, and may contain explicit or illegal content. These emails often use scare tactics, contain typos and misleading information, and are sent in bulk from an anonymous sender. They seldom contain an unsubscribe link, and if it does, that link may be embedded with malware. This could lead to cybercriminals gaining access to your computer, smartphone, and other devices.
There are ways to help slow the tide of unwanted emails. So, here are the five simple ways you can take to help eliminate spam emails.
1. Mark as spam
Most email services, such as Gmail, Yahoo Mail, Microsoft Outlook, and Apple Mail have algorithms that filter out spam and junk mail by tucking them away in a folder.
But if you find a spam email in your regular inbox, don’t delete the message — mark it as spam. Marking a suspicious email as spam will send it to the spam folder. Moving forward, if you receive any more emails from this address, the spam filter will know no to let it into your inbox.
How to mark spam in Gmail
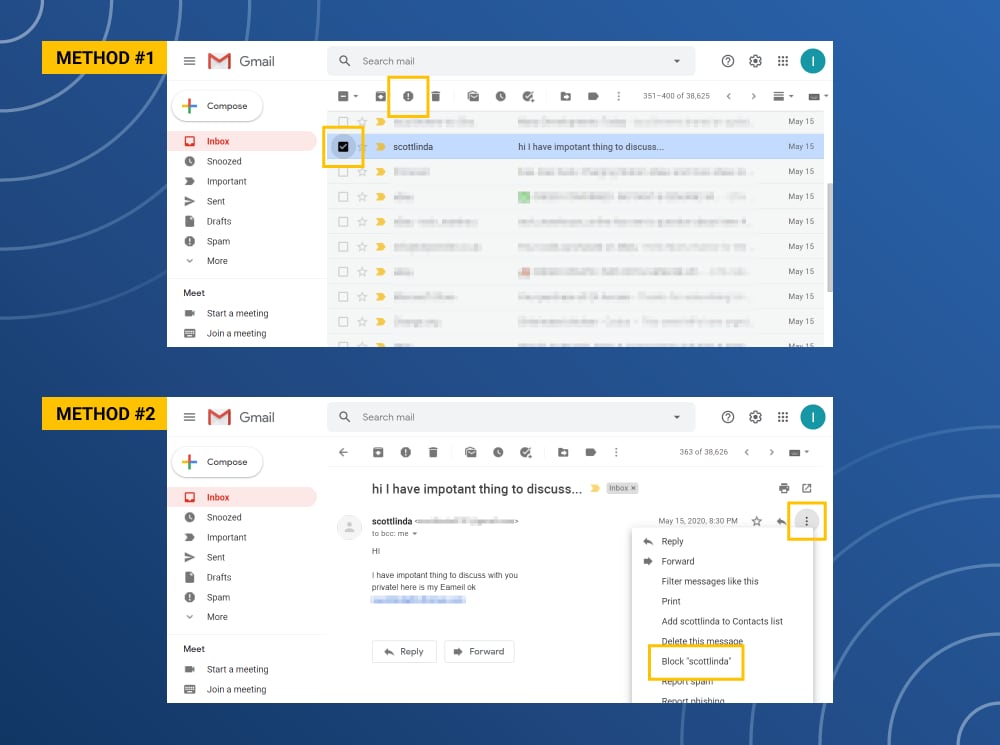
Click on the square next to the email → Click the stop sign icon
How to mark spam in Yahoo! Mail
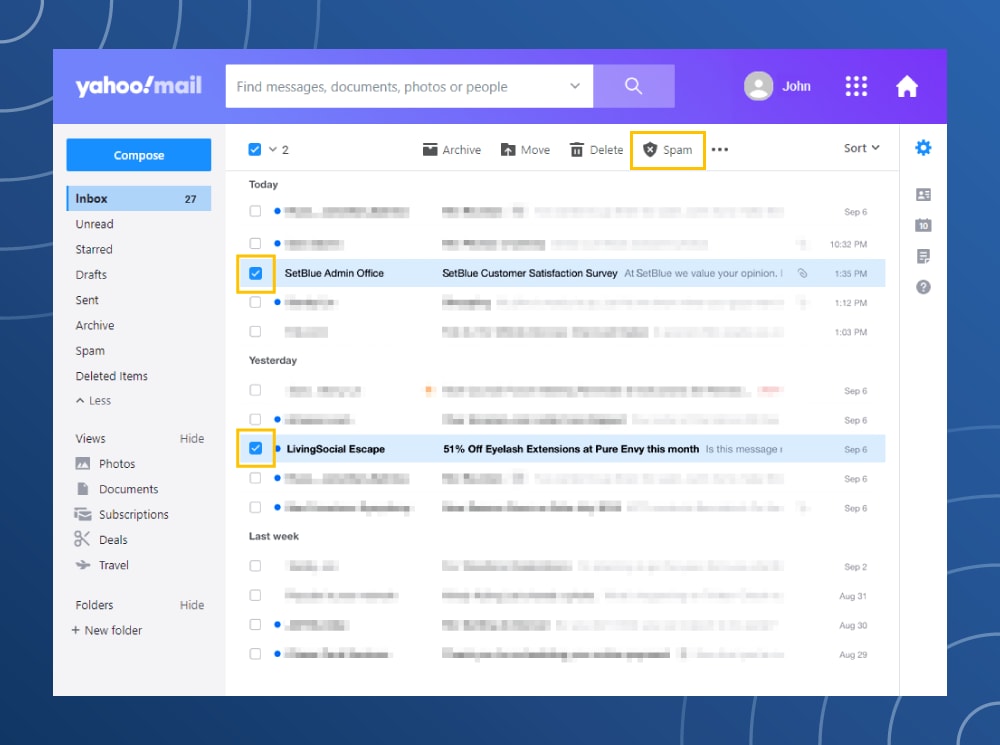
Click the box next to the email or on multiple emails → Click on the shield icon
How to mark spam in Microsoft Outlook
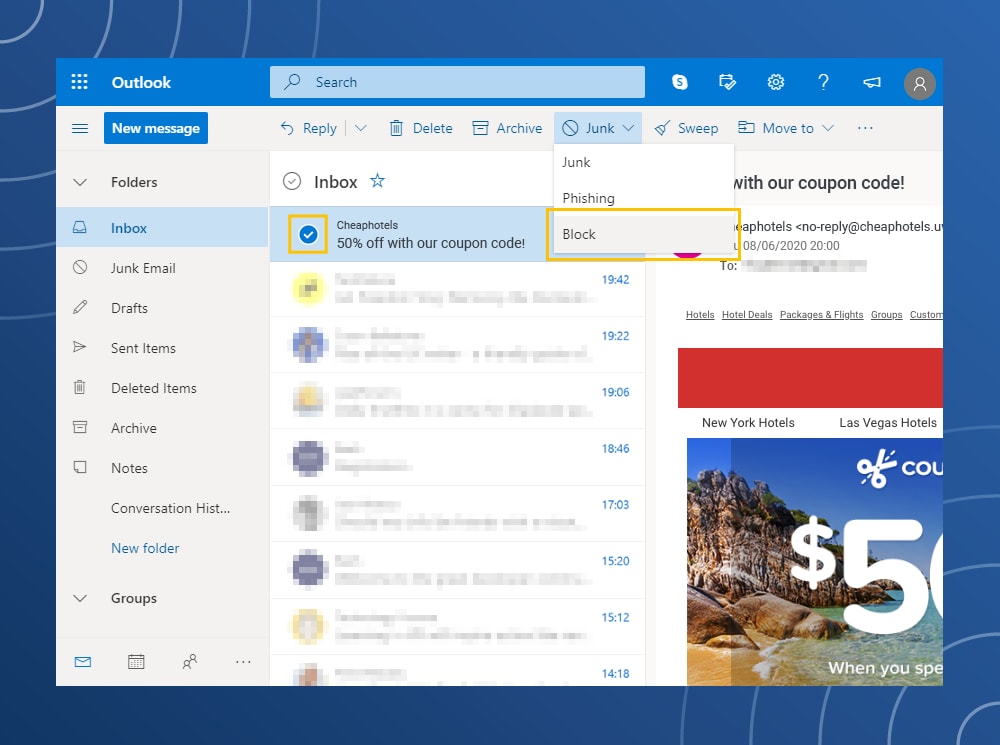
Click on the box next to the email → Click on Junk Email Options in the menu → Click on the Block button
How to mark spam in Apple Mail
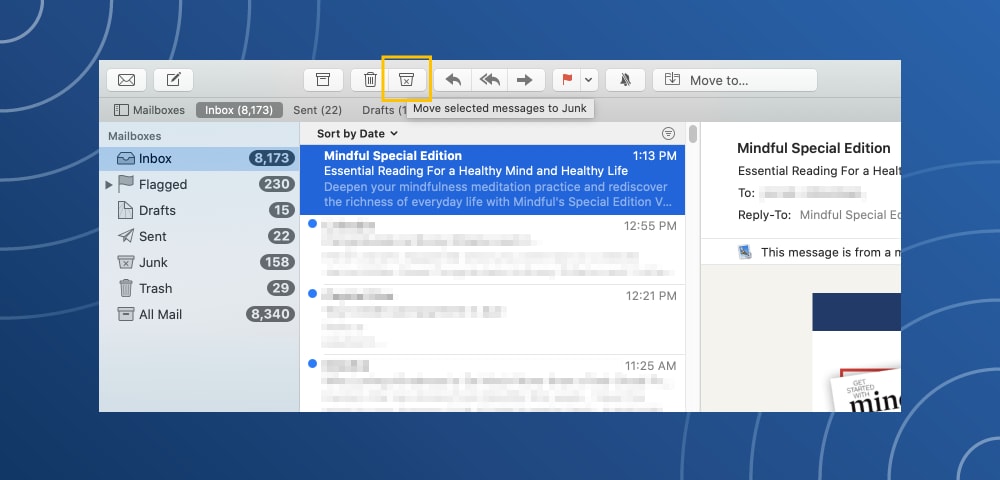
Click the email message → Click on the “X” marked trash can (Junk Mail) icon
A trained email filter can track and flag addresses that have been blacklisted or contain suspicious phrases like “cheap,” “Viagra,” or “free.”
2. Delete spam emails
There is a golden rule to dealing with spam emails: if it looks like a spam message, it probably is — so delete it without clicking or downloading anything. Such messages may contain software that tells the sender you’ve opened the email, confirming you have an active account, which may lead to even more spam messages.
Some malware programs can steal your email address and use it to resend spam messages under the guise of a legitimate address. For example, imposters could pose as someone you know, like a friend, relative, or colleague.
If the message in question appears to come from someone you know, contact them outside of your email.
Here are few options for deleting spam emails for good.
How to delete spam from Gmail
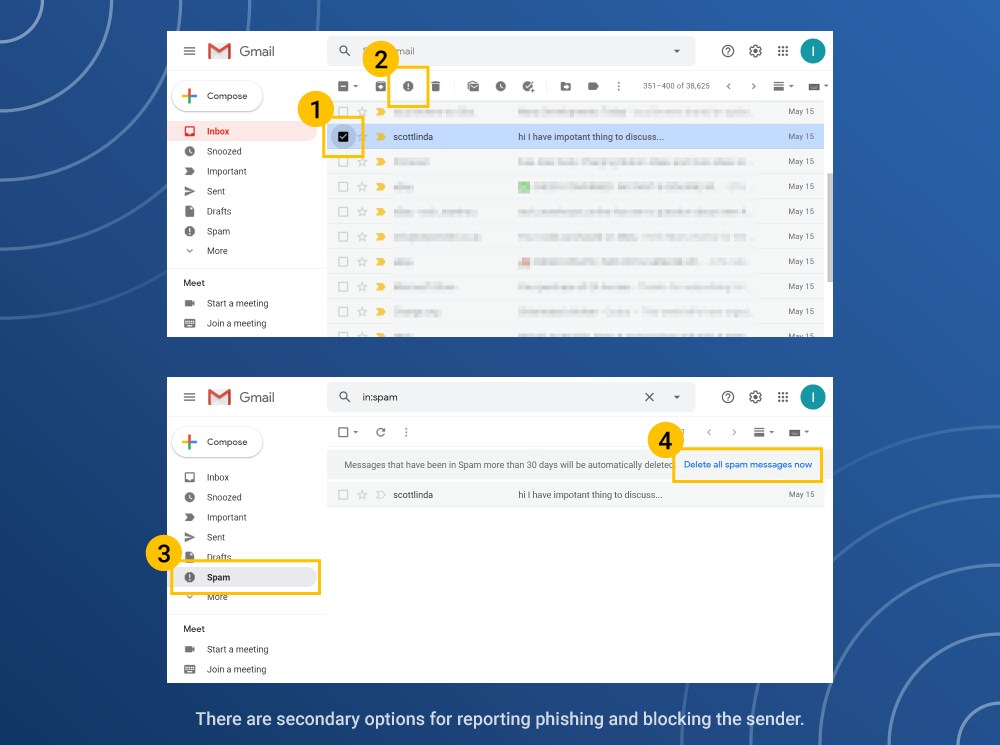
- Click on the empty box to check the message.
- In the top menu click on the stop sign.
- In the dropdown menu, click Report Spam.
- Click on the Delete All Spam Messages Now option.
Detailed instructions are available on Google’s support page.
How to delete spam from Yahoo! Mail
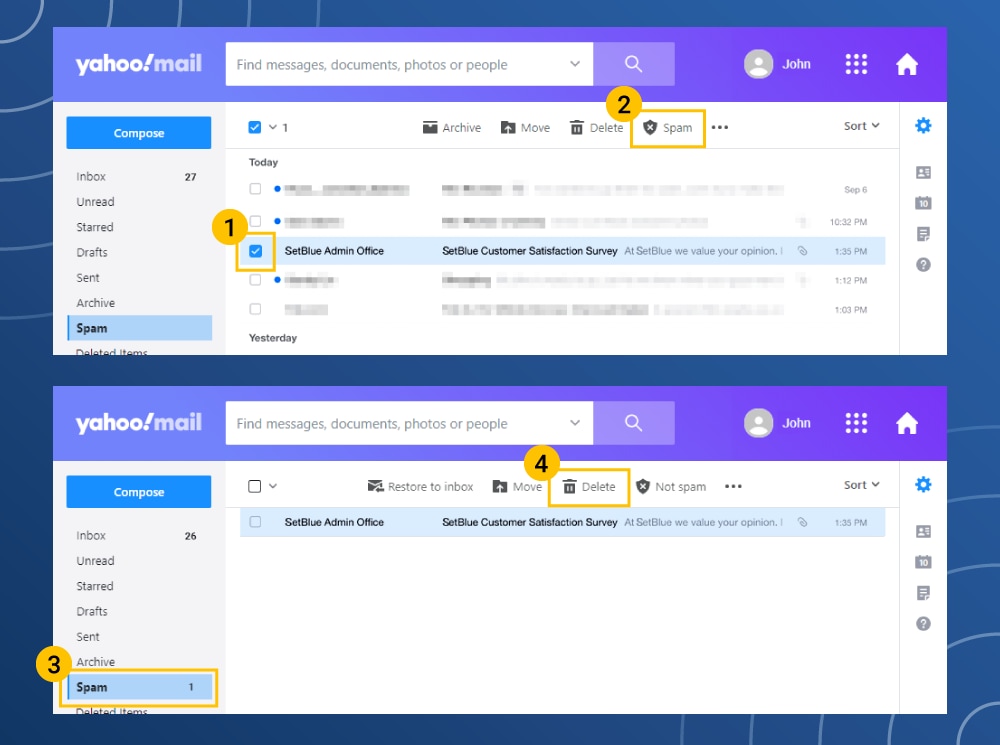
- Check the box next to the email.
- Click on the shield in the above menu.
- Click the Report Spam option.
- Navigate to the spam folder.
- Click the Delete Emails option.
Detailed instructions are available on the Yahoo! help page.
How to delete spam from Microsoft Outlook
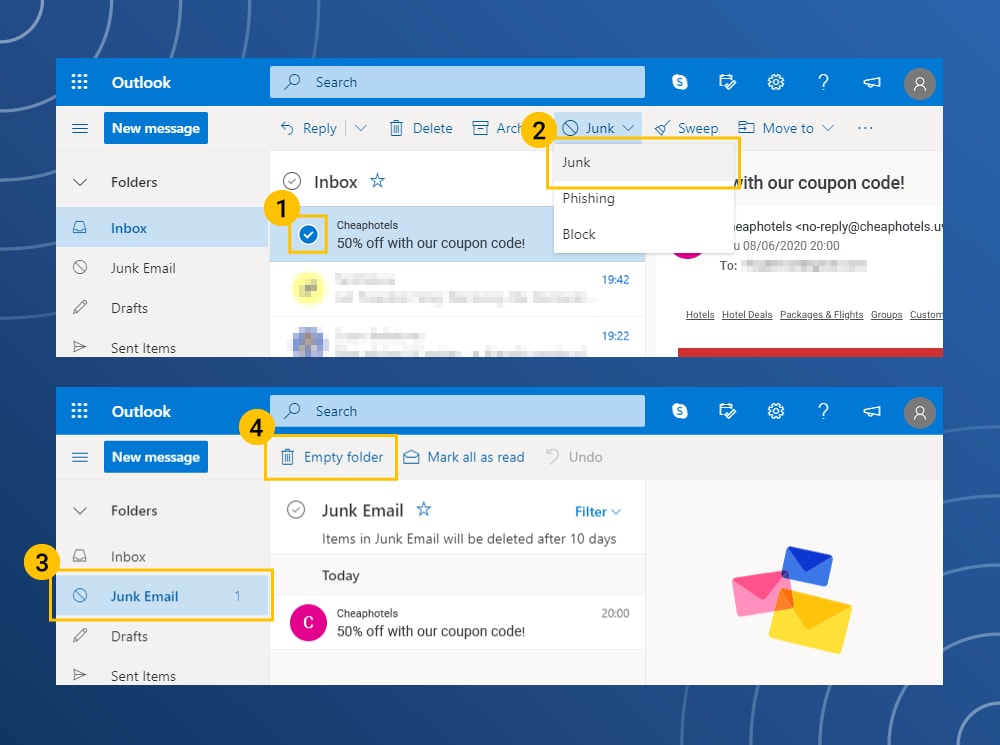
- In the inbox area, click the email.
- In the top menu, click on the Junk Mail option.
- Click on the Junk Email tab in the side menu.
- Click the metal trash can to empty the folder.
Detailed instructions are available on the Microsoft Office support page.
How to delete spam from Apple Mail
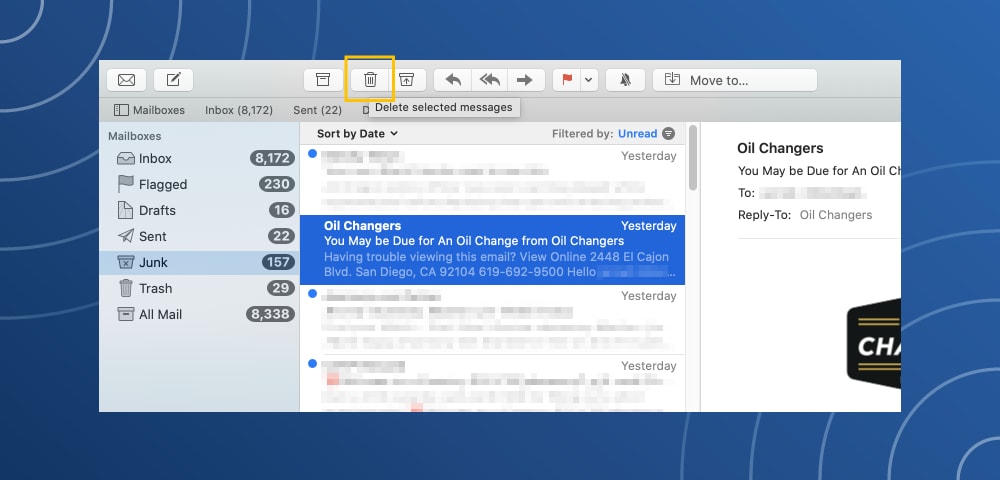
- Select the Junk Mail option in the left side menu.
- Highlight the desired messages.
- Click on the metal trash can (Delete selected messages) icon.
Detailed instructions are available on the Apple support page.
When you block spam messages, they’re sent to a spam folder. Over time, this folder grows with the flagged messages. So, you’ll want to occasionally empty.
While not completely fool- proof, here are five key factors to look for in a suspicious email.
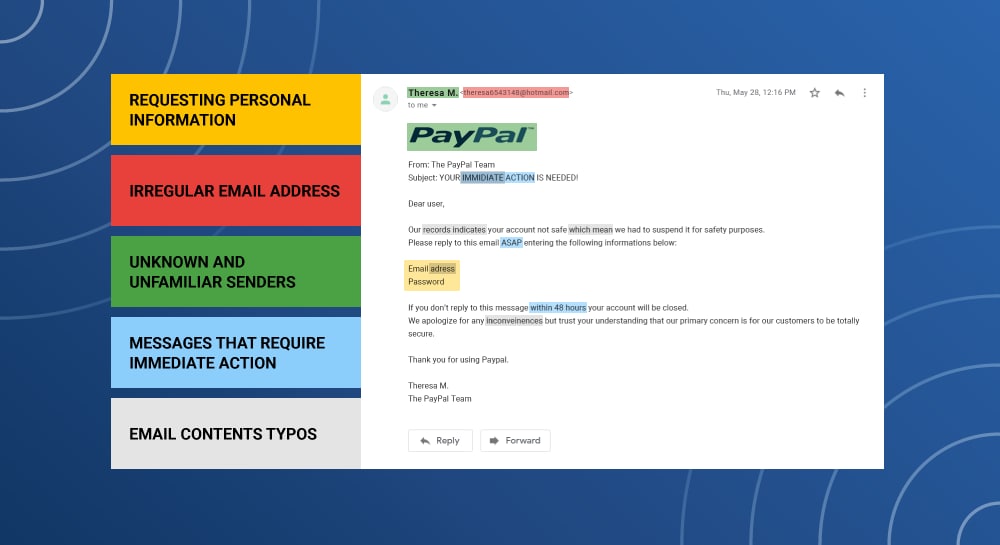
- Requesting personal information
The sender requests your personal information like address, Social Security number, or banking information.
- Irregular email address
The email has a suspicious domain name or uses uncommon characters in the address.
- Unknown and unfamiliar senders
Fake emails from people posing as influencers, high-ranking officials or legitimate companies. These companies may claim you’ve made purchases when you haven’t.
- Messages that require immediate action
These emails contain action words like, “Immediate,” “Limited Time,” and “Urgent” in the title box or subject line.
- Email contains typos
Many fake emails will contain basic typos and errors like misspelling your name or have poor grammar usage.
3. Keep your email address private
Giving out your email address can increase the amount of spam email you receive. So if it’s not essential to share, keep it private. Also, consider changing your email privacy settings. Here’s how:
Google Privacy Settings
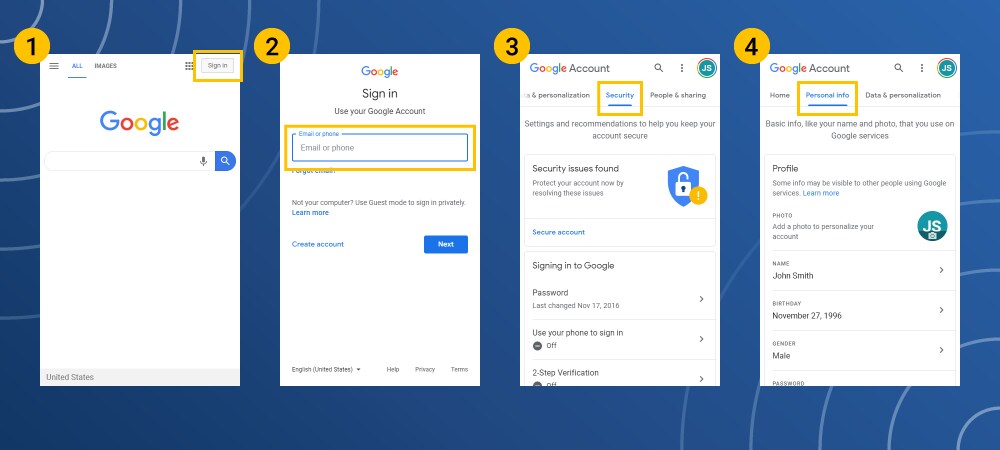
- Log-in to your Google account.
- Go to the Security Checkup option to see the devices, security events and other email addresses and devices connected to your Gmail account.
- Adjust the toggle switches to turn features on or off.
- Perform the same process for the Personal Information and Privacy settings.
Yahoo! Mail privacy settings
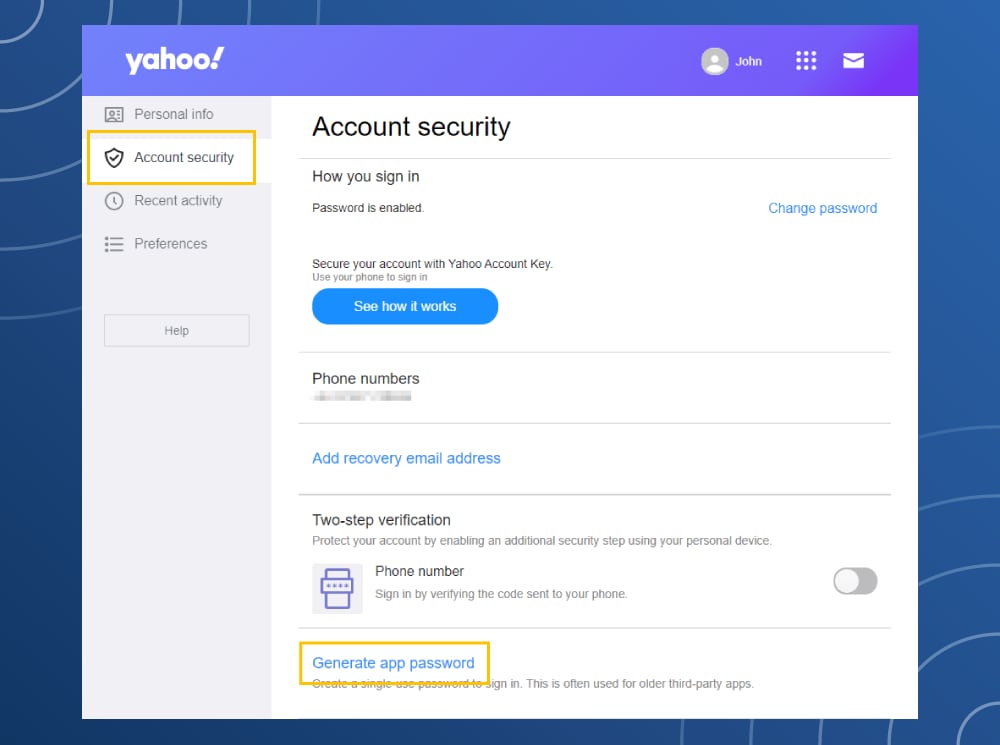
- Log-in to your Yahoo! Mail Account.
- Click on the gear icon.
- Click the Account Information option.
- In the Account Security section, click on the Generate app password option.
Microsoft Outlook privacy settings
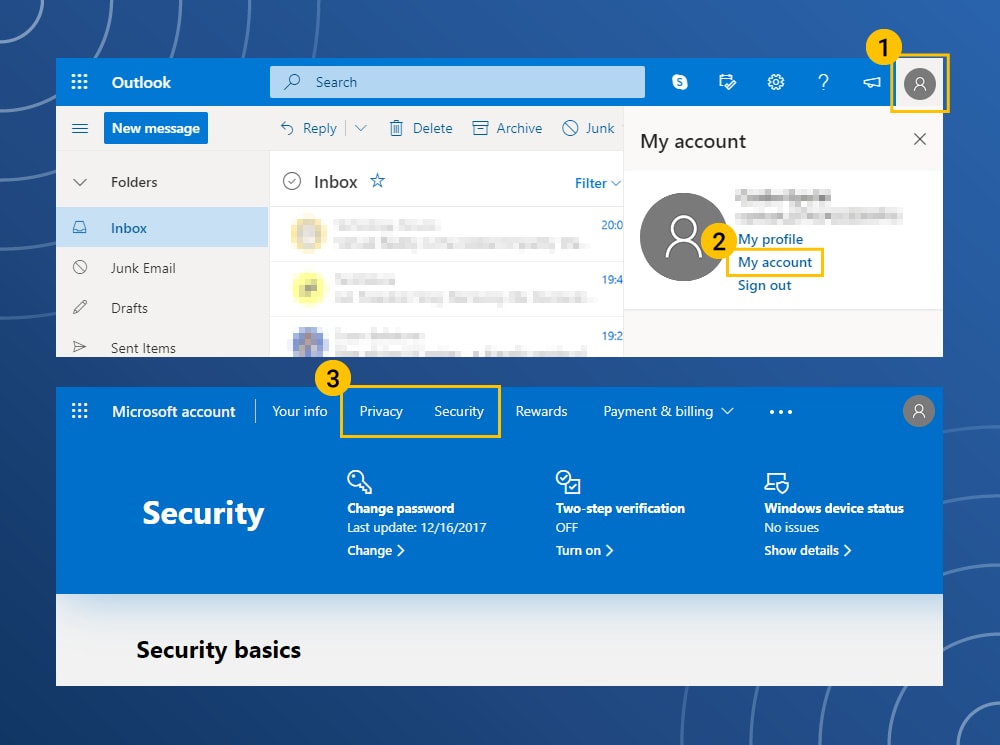
- Click on your account icon in the upper-right corner of the screen.
- In the menu list, click My Account.
- Click on the Privacy and Security options to change the settings.
Apple Mail privacy settings
- Click the apple icon in the upper left corner of the screen.
- Click on System Preferences.
- Click on the Security and Privacy option.
If you post on social media or leave online comments, don’t post your email. If you have no choice, it might help to create a separate email address to be used solely for social media purposes, thus helping to ensure your main email address remains private.
4. Use a third-party spam filter
Your email service provider may have its own filter but pairing it with a third-party spam filter can provide an additional layer of cybersecurity. The emails will travel through two spam filters to reach your inbox. So if it gets through one spam filter, the other should catch it.
Effective spam filters can protect your devices against malware threats, attacks, and undesirable content. Look for an anti-spam filter that works with your email provider and addresses your own needs.
5. Change your email address
If the spam keeps on rolling in, it could mean your email address was exposed in a data breach. It can be hard to prevent spam when cybercriminals have your information. One option in this case is to change your email address.
With free email services like Gmail, it’s easy to create multiple accounts so you can limit the spam that appears in your primary inbox. Here’s how:

- Start by registering for a new account with your current email service.
- Next, notify your contacts from your new account that you’ve changed email addresses.
- Finally, navigate to the Settings section and add the new email address to forward incoming emails from your old account.
How to add a forwarding address
After creating a new address, you may want to set it up so that you still receive emails from your old address. You can do this by adjusting the forwarding settings.
Forwarding your email address allows you to update your contact information on all accounts tied to your original email account. You can do it in four easy steps:
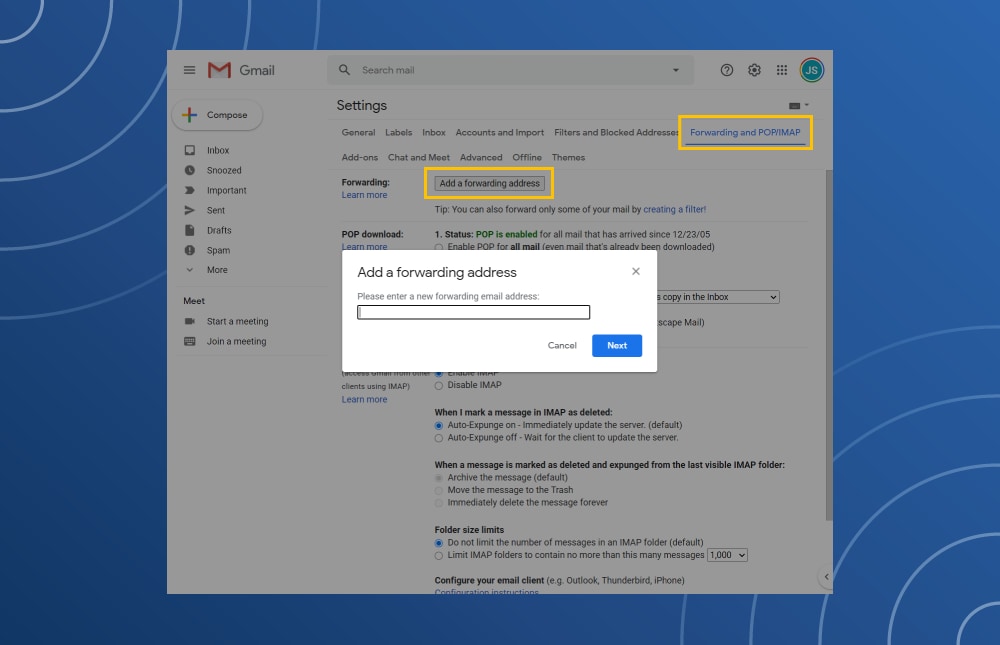
- In the old email account, go to the Settings option.
- Click the Forwarding and POP/IMAP tab.
- In the Add a forwarding address box, enter the new email address.
- Click “Next” to verify the process.
Be sure to keep both accounts open for a few months, so you can redirect any remaining messages to the new account.
6. Unsubscribe from email lists
Unsubscribing from email lists is an ideal way to keep a low profile. Marketers often get your email address from online forms, social media, and scraping tools, and purchase your information from other companies. So, the less you subscribe to, the less these marketers and spammers can find your address.
The Federal Trade Commission requires companies that send commercial or bulk emails to comply with the CAN-SPAM Act. Initiated in 2003, the law helps set rules and requirements for messages sent; one of the rules is that companies must always provide information for how to opt out of their emails. Non-compliance with these regulations can cost up to $43,280 in penalties from the FTC.
While the law doesn’t prevent marketers from sending spam emails, it does provide a way to stop them from filling your inbox. Here are two ways to unsubscribe from individual and bulk emails.
How to unsubscribe from individual emails
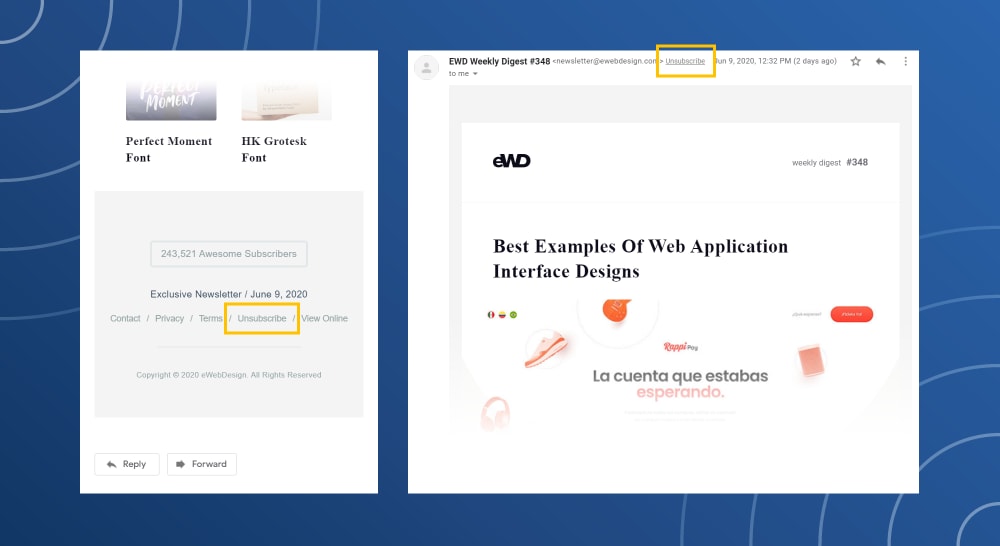
Most marketing emails will have unsubscribe buttons at the bottom of the email. Some email clients, like Gmail, will also show an unsubscribe button up at the top near the To: and From:.
How to unsubscribe from multiple emails
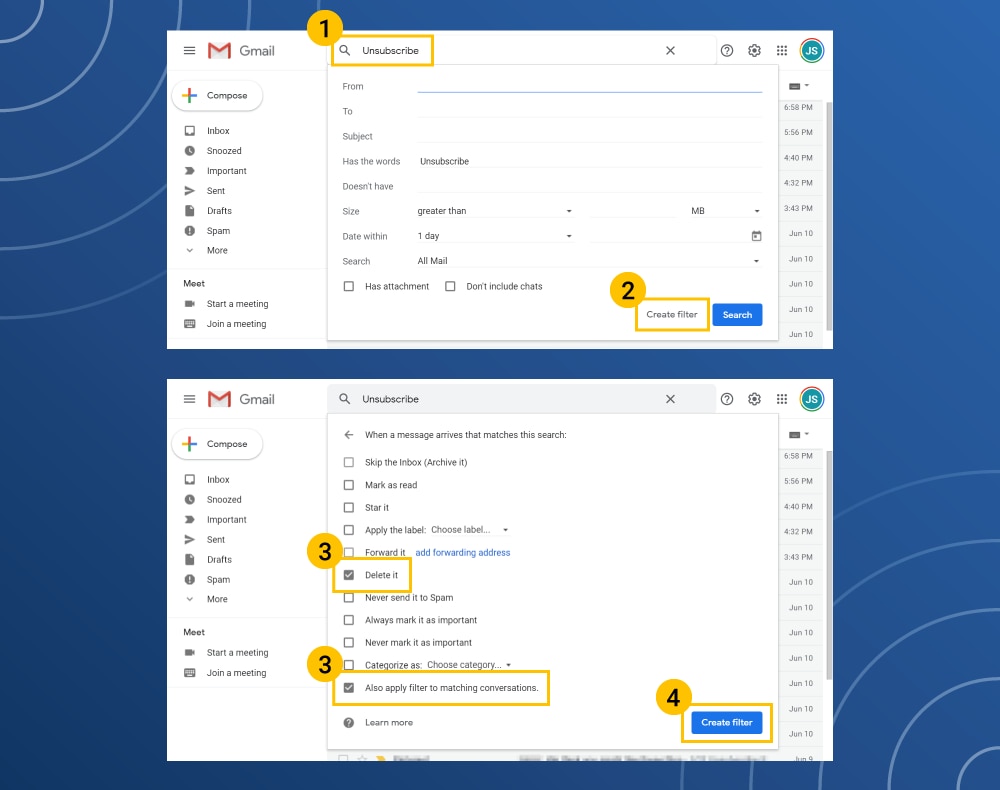
- In the inbox search bar, type “Unsubscribe.”
- Click the down arrow next to the box and click on the Create Filter button.
- Click the Delete and Apply Filter to Matching Conversations boxes.
- Create the filter.
This will move all the selected emails to the trash. In a few clicks, you’ve unsubscribed and eliminated multiple emails for good.
Now that you know how to look for and get rid of spam emails, it’s important to know the most common types of threats.
Common spam email security threats
Spam emails are annoying enough, but some of them can put your digital safety at risk. Some spam messages contain viruses, malware, and other cyberthreats. Here are a few to watch for.
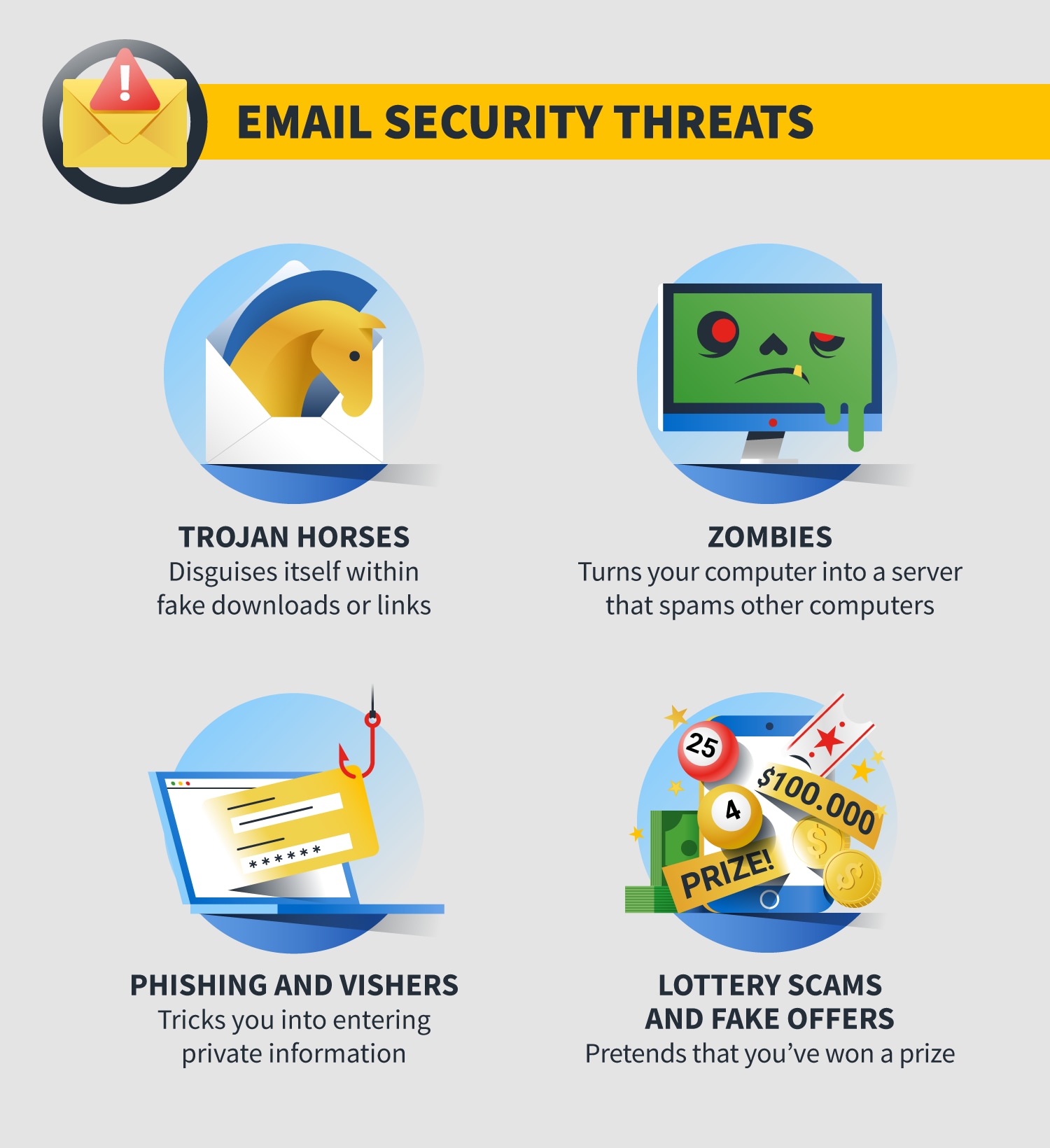
Trojan horses
Trojan horses come disguised as a legitimate program. Even if you think you know how to verify whether an email is legitimate, a trojan horse uses deception to get past those defense mechanisms.
For instance, they can hide inside free software downloads or arrive as an email attachment, possibly from someone you know.
When you open the email, the trojan installs malicious code — typically spyware or viruses — designed to create problems on your computer.
It may allow an attacker to control your computer, lock you out, steal your data, account information or email addresses. Installing anti-malware software may help you catch these trojans.
To help avoid trojan horses, avoid clicking on pop-up messages on your computer. If you are seeing a lot of pop-ups, consider running an antivirus scan.
Zombies
Zombies are a type of malware that also comes in email attachments. They turn your computer into a server and sends spam to other computers. You may not know that your computer is compromised, but it may slow down considerably or the battery may drain quickly. Meanwhile, your computer may be sending out waves of spam or attacking web pages.
One way to avoid zombies is to avoid opening attachments or clicking links in emails from your spam folder.
Phishing and vishers
Phishing emails often try to mimic messages from legitimate financial companies or other businesses you may use. The spam phishing email will ask you to go to a fraudulent or spoofed website to re-enter your credit card number or verify your password. It’s a scheme to capture that personal information.
Vishers will try to have you call them on the phone to provide your personal information. Keep in mind that reputable businesses would not make such requests by email or phone.
Perform a Google search on the company to verify legitimacy to avoid phishing scams.
For vishers, if you don’t recognize the number, let the caller leave a voice-mail message. Local or not, only respond to calls that are in your phone book.
Lottery scams and fake offers
Sometimes, cyber thieves use old-school scams that might seem legitimate but are fake offers. These play on your desires or good nature: You’ve won a lot of money or someone urgently needs your help.
In reality, you haven’t won a lottery or a cruise around the world. And you haven’t been selected by a foreign prince to receive $10 million, in exchange for the use of your bank account number.
Look for phrases of urgency like, “Immediate,” and “Act Now” in the email’s title to avoid lottery scams and fake offers. Refer back to the Delete Emails section of this post for additional characteristics to look for.
How to stay spam free
So far, there is no such thing as a “do not email” list for spam. Until there is, you’ll have to take care of spam yourself.
Fortunately, there are good tools to help you do that. Most email programs include spam filters that can help detect and isolate spam. Many internet service providers filter out spam, so it never reaches your computer. But it’s wise to install and run anti-virus security software that can eliminate viruses that may already live on your computer.
Should spam slip through these filters, take the simplest approach to suspicious emails and click Delete.
The practice of sending fraudulent emails purporting to be from reputable companies in order to induce individuals to reveal personal information, such as passwords and credit card numbers, or to click on links that install malware, is called phishing.

What is phishing? How to recognize and avoid phishing scams
Sept. 25, 2020
Ever get an email that looks like it’s from your bank warning you that it will freeze your checking account unless you verify your personal information? The email might have contained a link. And if you clicked? You might have landed on a website that asked you to fill in such personal information as your Social Security number and bank account numbers.
The problem? These emails never come from your actual bank. Instead, they’re a part of a scamming tool called phishing wielded by cybercriminals and a threat to your cybersecurity.
What is phishing?
Phishing is a cybercrime in which scammers try to lure sensitive information or data from you, by disguising themselves as a trustworthy source. Phishers use multiple platforms.

The ultimate goal no matter which method scammers use? They want your personal information so that they can use it to access your bank accounts or credit cards. And they’ll send countless fake email and text messages across the globe in the hope that they’ll trick enough people into surrendering this sensitive information.
Some phishing emails or texts might look unprofessional to you, using poor grammar or asking you to click on links with odd-looking URLs. But phishers don’t have to be sophisticated. These cybercriminals work in volume, and only need to trick a small number of victims to consider their work a success.
As an example, in 2018 the Federal Trade Commission pointed to a phishing attack targeting Netflix users. The phishing email purported to be sent from Netflix and warned recipients that the streaming company is “having some trouble” accessing the customer’s billing information. The message asked victims to click on a link to update their payment method. That link, of course, didn’t take users to Netflix but instead to a fake website created by the scammers.
How do you make sure you’re not one of these unlucky victims? It’s all about learning how to recognize phishing scams and resolving to never click on a link in a text or an email supposedly sent from a bank, credit-card provider, or other well-known company. And that doesn’t include all the phishing emails that get caught in your spam filter.
How does phishing work?
- The phisher begins by determining who their targeted victims will be (whether at an organization or individual level) and creates strategies to collect data they can use to attack.
- Next, the phisher will create methods like fake emails or phony web pages to send messages that lure data from their victims.
- Phishers then send messages that appear trustworthy to the victims and begin the attack.
- Once the attack has been deployed, phishers will monitor and collect the data that victims provide on the fake web pages.
- Finally, phishers use the collected data to make illegal purchases or commit fraudulent acts.
That being said, when defining what phishing is, not all attacks look and operate the same. Phishing scams can take a variety of forms and can have different goals in their deployment.
Types of phishing attacks and examples

Phishing scams can take a variety of forms. Some phishing emails will ask you to click on a link to prevent your bank account or credit card from getting closed. When you click on the link, you’ll be taken to a website that asks for your personal financial information. That could open the door to identity theft.
Other types of phishing attacks ask that you click on a link to verify that a credit card or bank account is yours. Again, that link will take you to a fraudulent website that will ask you to provide personal or financial information that will likely be captured by fraudsters.
You might receive a phishing email warning you that your email account is full and in danger of being shut down. Unless you click on a link, the email warns, you will lose access to your email messages. Again, links like this could request and capture your personal information or could install malware or adware onto your computer.
The unfortunate truth? There are many types of phishing attacks. You need to be on the lookout for all of them.
1. Email Phishing
The basic phishing email is sent by fraudsters impersonating legitimate companies, often banks or credit card providers. These emails are designed to trick you into providing log-in information or financial information, such as credit card numbers or Social Security numbers.
Other spoof emails might try to trick you into clicking a link that leads to a fake website designed to look like Amazon, eBay, or your bank. These fake websites can then install malware or other viruses directly onto your computer, allowing hackers to steal your personal information or take control of your computer, tablet, or smartphone.
A phishing example? You might receive an email that looks like it was sent by PayPal. The email might say that you need to click on a link to verify your PayPal account. If you don’t? The email says that your PayPal account will be shut down.
Here’s an example of a PayPal phishing email.
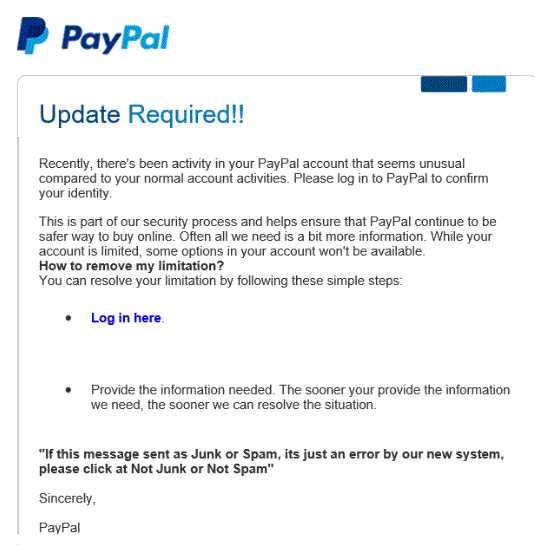
Source: Secure World
Of course, this is a scam. If you click on the link, you’ll be taken to a fake log-in page designed to look like it is PayPal. If you then enter your password and username, the scammers will capture this information.
These emails often feature spelling errors, odd grammar, and generic greetings such as “Dear User” or “Dear client.” The links you are supposed to click will often lead to websites with odd URLs or ones that are spelled just a bit differently from the institution’s legitimate website.
PayPal, credit card companies, mortgage lenders and banks will never contact you by email to request any personal information from you. Instead of clicking on links in emails, log into your account on your own. If there is a legitimate concern, you’ll see it when you log in.
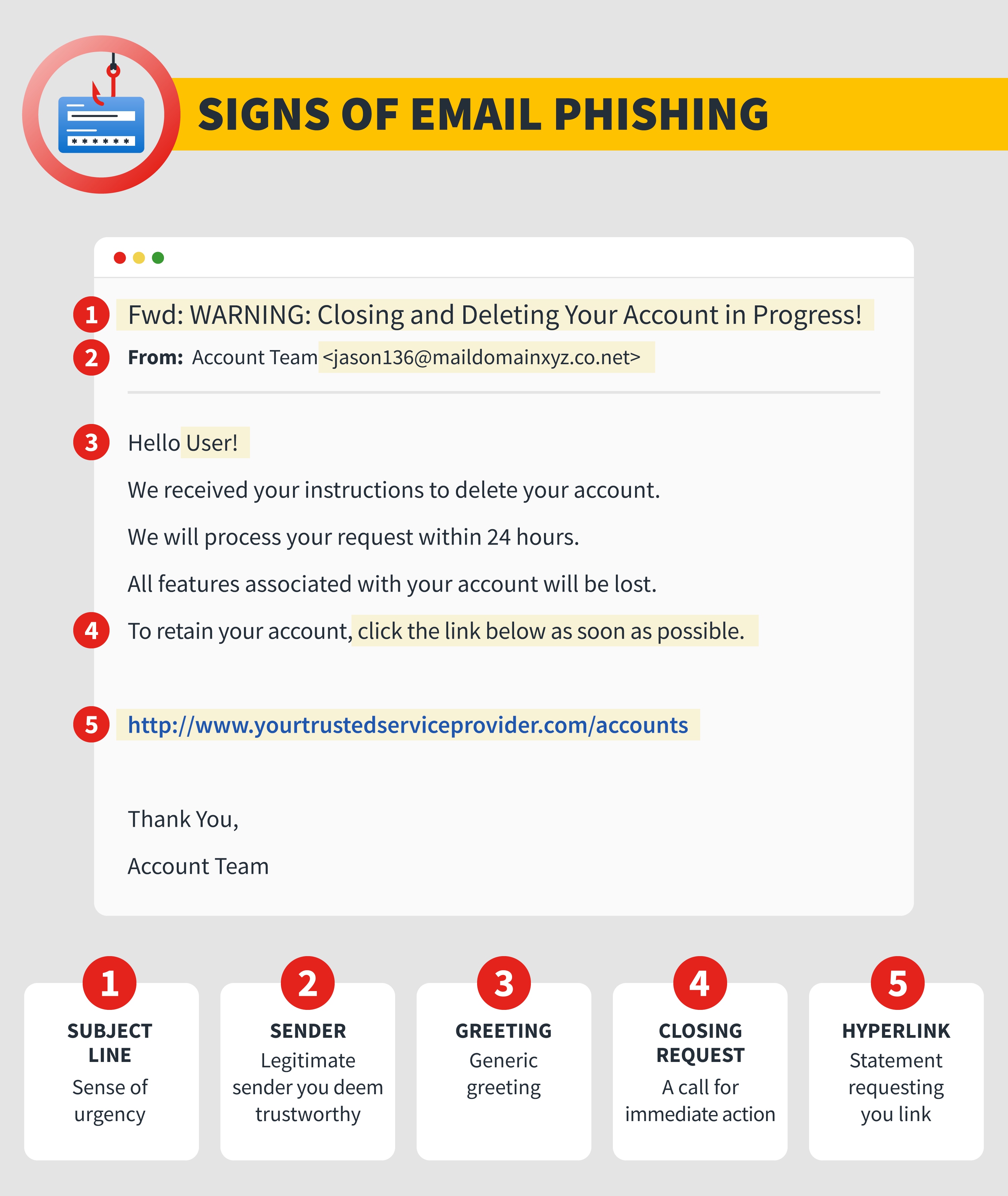
How to recognize phishing emails
Scammers have become more sophisticated when it comes to sending out phishing emails. But there are still some signs you can look for.
- Too good to be true offers. Phishing emails may try to hook you with what appears to be incredibly cheap offers for things like smartphones or vacations. The offers may look irresistible but resist them. They’re likely phishing emails.
- A bank — maybe not even your own — is asking for your account information or other personal financial information. Your bank, or any financial institution, will never ask for your Social Security number, bank account number, or PIN by email. Never provide this information in response to an email.
- Spelling and grammatical mistakes. There was a time when you could easily spot phishing emails because they were littered with spelling and grammar mistakes. Scammers have gotten better at avoiding these errors, but if you do receive an email littered with typos and weird language, that email might be sent from someone phishing.
- The generic greeting. Phishing emails might not be addressed specifically to you. Instead, the email might start with a generic greeting such as “Dear Sir or Madam” or “Dear Account Holder.”
- A call for immediate action. Phishers want you to act quickly, without thinking. That’s why many will send emails asking you to immediately click on a link or send account information to avoid having your bank account or credit card suspended. Never reply hastily to an emergency request. Urgent requests for action are often phishing scams.
- Senders you don’t recognize. If you don’t recognize the sender of an email, consider deleting it. If you do decide to read it, be careful not to click on links or download files.
- Senders you think you recognize. You might get a phishing email from a name you recognize. But here’s the catch: That email may have come from the compromised email account of someone you know. If the email requests personal information or money, it’s likely it’s a phishing email.
- Hyperlinks. If you receive an email that requests you click on an unknown hyperlink, hovering over the option might show you that the link is really taking you to a fake, misspelled domain. This link is created to look legitimate but is likely a phishing scam.
- Attachments. The sender included attachments that don’t make sense or appear spammy.
2. Spear phishing
While most phishing emails are sent to large groups of people, there is one type of attack that is more personalized in nature, spear phishing.
Spear-phishing emails are targeted toward a specific individual, business, or organization. And unlike more generic phishing emails, the scammers who send them spend time researching their targets. The technique is sometimes called social engineering. These criminals will send emails that look like they’re from legitimate sources.
For instance, in 2016, millions of customers who had made a purchase from Amazon received an email with the subject line “Your Amazon.com order has been dispatched” with an order code after it. When consumers opened the email, there was no message, just an attachment. If they opened the attachment, consumers ran the risk of installing ransomware on their computers.
In another spear-phishing example, emails might target a company employee. The email may appear to come from the boss, and the message requests access to sensitive company information. If the spear-phishing target is tricked, it could lead to a data breach where a company or employee’s information is accessed and stolen.
3. Clone phishing
Another type of phishing, clone phishing, might be one of the most difficult to detect. In this type of phishing attack, scammers create a nearly identical version of an email that victims have already received.
The cloned email is sent from an address that is nearly, but not quite, the same as the email address used by the message’s original sender. The body of the email looks the same, too. What’s different? The attachment or link in the message has been changed. If victims click on those now, it will take them to a fake website or open an infected attachment.
4. Whaling
Sometimes phishers go after the biggest of targets, the whales. Whaling attacks target chief executive officers, chief operating officers, or other high-ranking executives in a company. The goal is to trick these powerful people into giving up the most sensitive of corporate data.
These attacks are more sophisticated than general phishing attacks and require plenty of research from scammers. They usually rely on fraudulent emails that appear to be from trusted sources within the company or from legitimate outside agencies.
5. Pop-up phishing
Pop-up phishing is a scam in which pop-up ads trick users into installing malware on their computers or convince them to purchase antivirus protection they don’t need.
These pop-up ads sometimes use scare tactics. A common pop-up phishing example is when an ad might pop up on a user’s screen warning the user that their computer has been infected and the only way to remove the virus is by installing a particular type of antivirus software.
Once the user installs this software, it either doesn’t work or, worse, actually does infect the computer with malware.
How to report phishing
If you’ve been victimized by a phishing scam, you should alert the proper authorities. You can report a phishing attempt or crime to the Federal Trade Commission at its Complaint Assistant page. You can also report the attack to the Anti-Phishing Working Group or forward the phishing email at reportphishing@apwg.org. If you receive a phishing text message, forward it to SPAM (7726).

How can I protect myself from phishing attempts?
Though hackers are constantly coming up with new phishing techniques, there is good news. There are some things that you can do to protect yourself and your organization. All it requires is some common sense.
- Don’t open suspicious emails. If you receive an email supposedly from a financial institution with an alarming subject line — such as “Account suspended!” or “Funds on hold” — delete it. If you are worried that there is a problem, log in to your account or contact the bank directly. If there really is a problem with your bank account or credit card, you’ll find information once you’ve logged in.
- Don’t click on suspicious links in emails. If you do open an email from someone you don’t know and you are instructed to click on a link, don’t. Often, these links will take you to fake websites that will then encourage you to either provide personal information or to click on links that might install malware on your computer.
- Don’t send financial information through email. Your bank or credit card provider will never ask you to provide bank account numbers, your Social Security number, or passwords through email.
- Don’t click on pop-up ads. Hackers can add fraudulent messages that pop up when you visit even legitimate websites. Often, the pop-ups will warn you that your computer is infected and instruct you to call a phone number or install antivirus protection. Avoid this temptation. Scammers use these ads to either install malware on your computer or scam you out of a payment for a computer clean-up you don’t need.
- Use spam filters. Spam filters can help block emails from illegitimate sources, but you should always use your best judgment in case phishing emails get past your blocker.
- Sign up for antivirus protection. Make sure your computer is protected by strong, multi-layered security software.
Installing and running trusted security software may provide real-time threat protection, help you create and manage unique passwords, and help protect your personal files and financial information from phishing attacks and other scams.
How to recover after responding to a phishing email
What if you’ve fallen for an email scam? Perhaps you sent financial information to a scammer or clicked on a link that installed malware on your computer.
You’ll want to act quickly. Here are some steps you can take if you’ve been responded to a phishing scam to help protect yourself against identity theft.
- Change your passwords: Make sure to change the passwords you use for your banking, credit card and other accounts. Use a combination of numbers, letters and symbols to make these passwords more difficult to crack. Consider enabling multi-factor authentication if it’s available. Multi-factor authentication requires entering a second piece of information — such as a code sent to your smartphone — to access an account.
- Alert the credit bureaus: Visit the home pages of Experian, Equifax, and TransUnion, the three national credit bureaus, and alert them that you’ve been the victim of a phishing attempt. You might freeze your credit with each of the bureaus to make sure that criminals can’t open new credit accounts or take out new loans in your name.
- Contact your credit card providers: If you’ve given up credit card information, immediately call your credit card providers. They can freeze your credit to prevent unauthorized purchases. They can also work with you to determine which purchases on your accounts are legitimate and which were made by criminals.
- Check your credit reports: Order free copies of your credit reports from AnnualCreditReport.com. Check these reports carefully for any unfamiliar activity to make sure no one has opened credit card accounts or loans in your name.
- Study your credit card statements: Be on the lookout for any unauthorized or suspicious charges.
As cybercriminals continue to evolve their phishing attacks and other techniques, its best to have advanced security software leading your defense. To ensure you aren’t asking yourself “what is phishing” after an attack has already unfolded, make sure to take the precautions and use your best judgment when browsing online and responding to messages.
While antivirus protection is one of the keys to limiting risk, the right VPN can encrypt the network traffic you send and receive and hide your IP address, providing an additional layer of online privacy.
